One of the greatest app development problems is the balance between ease of use and functional load. The latter represents the set of use cases supported by the application. The larger the set, the more complex the user interaction.
Many of the security features, like user authentication or the confirmation of a sensitive operation, involve additional user actions. These actions can be reading the fingerprint, entering a password and so on. These actions are also part of the functional load and affect usability.

What is an intuitive user interface?
Some examples of simple apps are the flashlight and the compass. The user interaction is simple because the functionality is minimal. Probably nobody needs to read a manual to learn how to use the flashlight or play Tetris. On the other hand, the Android Settings app has hundreds of options. Many of them require technical knowledge. Achieving an intuitive user experience in a complex application is a significant challenge, even for Google developers.
The user interface is intuitive if the average user can easily understand it, without prior training. Intuitive and user-friendly are different concepts, although they often qualify the same interaction. For example, rotary knobs simulating a safe lock can be intuitive, but more complex than the numeric keypad, to enter a PIN.
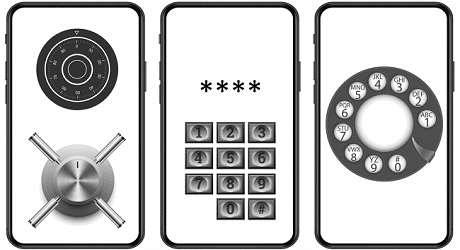
A rotary dial on the old analog phones is very simple, but it might not be intuitive as many people have not seen or do not remember them today.
Web-app interfaces
Currently, the use of web-app interfaces is rather common. There are also hybrid interfaces, where part of the implementation is web-app and the rest is native. Web-app interfaces are generated by a web server and are deployed within the application in a similar way to web browsers, such as Chrome. Their popularity is due to the following main factors:
- It is possible to make changes to the interface in a centralized way. There is no need to publish a new app version and wait for the users to apply the update.
- The same code base can be used for the web interface and the app. It reduces development and maintenance costs.
From the security point of view, web-app interfaces may have more advantages:
- If fixing a vulnerability at the web-app level is possible, without modifying the native code, the mitigation time is much shorter. Therefore, the impact can be less critical.
- Hacking a solution running on a remote server is harder, because the access is limited to the user interface only.
Web servers are vulnerable as well. A web-app can also be insecure. In general, however, remote code in the cloud can be more secure than native code running locally.
The user experience with web-app interfaces can be less optimal, as the interface can take some time to download, especially if the internet connection is slow. Using the Internet consumes bandwidth and battery. Consider implementing a web-app interface only if the application requires connectivity, such as banking apps, social networks and so on.
Security vs. user-friendliness
The biggest challenge is improving security without affecting the user experience. For example, the use of biometrics, such as fingerprint or facial recognition, instead of memorizing passwords, can simplify the user interaction. The use of biometrics does not require developing complex AI algorithms. These algorithms are already available in hardware or Android API.
Another example is authentication based on user behavior recognition.1 The goal is to analyze user behavior, which includes touch screen manipulation (position, speed, sliding angle), usage frequency and duration, among other variables. Some commercial implementations are available already. In fact, the idea of profiling the user behavior for authentication purposes is not new. Experimental implementations have been around since at least 2016.2
The effectiveness of these implementations can be 75% or higher. By combining these behavioral profiles with other factors, such as biometrics and traditional keys, it's possible to achieve a higher level of reliability.
However, it is important to remember that users can change their habits. Furthermore, authentication is only one of the security aspects. The user's identity impersonation is only one of the fraud methods. Other methods consist of intercepting the communication channels, exploiting vulnerabilities, reverse engineering and so on.
The weakest link
The philosopher Thomas Reid wrote, “A chain is only as strong as its weakest link”. This phrase applies perfectly to computer security, including mobile services. It is important to keep auditing each of the modules or processes involved in the service. Reducing the number of links in the chain helps minimizing the risks as well.

The weakest link can be the user, who writes down his password and keeps it in a visible place. The use of less secure protocols for compatibility with old devices or previous app versions can also become a vulnerability.
A colleague who develops drivers for Windows says that sometimes the most innocent change in the code can have disastrous effects. Mobile apps development is susceptible to this kind of issues as well, although to a lesser extent. Strict version and change control, combined with extensive QA testing, reduces the likelihood of bugs, including security bugs.
Large software companies have security specialists or information security officer. Allocating specialized resources to security helps reducing risks. Security is less visible than usability or functionality. That's why it doesn't always receive the necessary attention throughout the development cycle. Moreover, the developers are not always security experts. Therefore, if the development team does not have security specialists, training them is necessary. Most of the app vulnerabilities appear due to the lack of expertise or carelessness.
References
- Adnan Ali, Vasaki Ponnusamy, Anbuselvan Sangodiah (2019), «User Behaviour-Based Mobile Authentication System», DOI:10.1007/978-981-13-6861-5_40
- Hassan Sbeyti (2016), «Mobile user authentication based on user context and behavioral pattern (MOUBE)», Arab Open University


